Customers are running their internal Certificate Authorities to present a secure environment to their users. Often, ESXi hosts do have default VMware certificates installed as in most environments, only vSphere administrators connect directly to ESXi hosts directly.
But recently, I had several customers requiring certificates for their ESXi hosts. So I needed to prepare my lab to be able to check details and installed a Root CA and an Enterprise Sub CA.
In this blog, I will implement a VMCA as Sub CA to be able to have certificates for my hosts as well.
CA Implementation
I am running a couple of Windows Server 2019 like Domain Controller, Global Catalog Server, Root CA Server, and Enterprise CA Server.
I am using RSA as signature algorithm and sha512 as signature hash algorithm.
Generating a Server Key
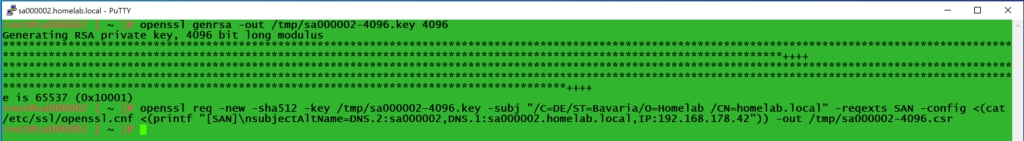
First thing is to create a server key on the console of the VCSA:
openssl genrsa -out /tmp/sa000002-4096.key 4096
Generating a Certificate Signing Request
Second thing is to create the .csr file.
openssl req -new -sha512 -key /tmp/sa000002-4096.key -subj “/C=DE/ST=Bavaria/O=Homelab /CN=homelab.local” -reqexts SAN -config <(cat /etc/ssl/openssl.cnf <(printf “[SAN]\nsubjectAltName=DNS.2:sa000002,DNS.1:sa000002.homelab.local,IP:192.168.178.42”)) -out /tmp/sa000002-4096.csr
Requesting the Certificate
1. Copy the content of the .csr into Submit a Certificate Request Dialogue
Make sure to use the Subordninate Certification Authority as Certificate Template:

Download the certificate as Base 64 encoded file and transfer back to the same directory on the VCSA.
2. Create the Certificate Chain
The structure of the certificate looks like this:

So copy the content to a new .cer file and copy this file back to the same directory on the VCSA.
3. Certificate Manager
With the second option, follow the dialogue to replace VMCA root certificate.

Enter required information:

Continue with the import (Option 2):

After some time, all is done:

What I recognised here is that the certificate is now with 2048 Bits ans sha256. I need to dig into that deeper what options are required for sha512/4096 Bits and will update this article.
4. Certificates for ESXi Hosts
You are only required to do a Renew Certificate in the context menu.

Hope that helps!
